- Simple Phishing Toolkit provides an opportunity to combine phishing tests with security awareness education, with a feature that (optionally) directs phished users to a landing page with an awareness education video. Moreover, there is a tracking feature for users who completed the training.
- Phishing software, free download. PH7 Social Dating CMS (pH7Builder) ️ pH7CMS is a Professional, Free & Open Source PHP Social Dating Builder Software (primarily designed.
- Actually, phishing is the way for stealing someone detail like password of any account. Snapchat is a next-level social media app. It is totally different from Facebook, Instagram, etc. In this phishing attack method attackers simply create a clone website of any website like Instagram, Facebook, Gmail, Twitter, etc.
While it’s a well-known concept, we’ve recently seen the growing sophistication of phishing campaigns, making detecting phishing domains harder, increase of spear phishing in APT attacks, and the increasing use of customized, targeted emails that ensure these campaigns are more successful than ever. Even if almost everyone nowadays is aware of possibly getting phished, by opening emails that contain links or other attachments.
Regardless of this understanding many have of phishing attacks, human error remains the top cause of data breaches; and phishing, which exploits human psychology, continues to be one of the most devastating threats to enterprise security. Organizations need to provide regular assessments, not only to address gaps in the cybersecurity culture and to increase awareness amongst their employees, but also to examine their technical infrastructure more effectively.
Red team operations cover different aspects of organizations’ security posture, so social engineering, and phishing in particular, are always covered in their assessments. Phishing tools and simulators are often used by red teams during red team assessment, when a red team takes on the role of “attacker” to research targets and craft phishing campaigns, all to test the organization’s readiness for attack and susceptibility to phishing.
Best fake page maker work with Ngrok it has 17 different type of phishing page - FDX100/Phisher-man. Phishing Page Maker Tool Make Own Icon Button For Cockos Reaper Short Bytes: The security researchers at PhishLabs have uncovered a new type of Facebook phishing attack that uses the URL Padding technique. The tactic targets the mobile users and fools them by making the deceptive links look authentic. As a result, casual users end up visiting.
Download autodesk inventor 2010 full crack. Recently, we went over the perfect red team tools for your security toolkit, and we mentioned phishing tools in the weaponization phase of the red team operation’s attack approach. Today we’ll go deeper, delving into different types of red teaming and their tools for dealing with phishing: simulators, reverse proxies, frameworks, scripts and more.
Top phishing tools to audit your enterprise security
The following list of phishing tools is presented in no particular order. We’re favoring open source projects, with a few commercial solutions that are aimed more directly at enterprise security training and e-learning. One important note before we start: the tools in this list are not to be used without previous authorization by the owners of network/systems tested, and are to be used for educational purposes only.
King Phisher
Let’s start with one of the better-known open source phishing campaign tools, one that was included in our post about red team tools. King Phisher is written in Python, and as we mentioned, it’s a free phishing campaign tool used to simulate real world phishing attacks and to assess and promote an organization’s cybersecurity and phishing awareness.
A frequent tool of red team operations, King Phisher allows you to create separate phishing campaigns with different goals, whether it’s for simple phishing awareness, or for more complex situations where it’s used for credential harvesting. Its ability to capture credentials and different numbers of targets, is impressive—sometimes reaching 10k targets per campaign. And as King Phisher has no web interface, it can be difficult to identify its server, and whether it’s used for social engineering. This reduces its exposure to web vulnerabilities such as XSS.
Other features include:
- Graphs of campaign results
- Embedded images in emails
- Optional 2FA
- Templates using the Jinja2
- SMS alerts on campaign status
- Web page cloning
- SPF checks
- Geo location
Gophish
Let’s continue with another tool that has made its way from the red team toolkit: Gophish. An open source phishing simulator written in GO, Gophish helps organizations assess their susceptibility to phishing attacks by simplifying the process of creating, launching and reviewing the results of a campaign.
Gophish can help you create email templates, landing pages and recipient lists, and assists in sending profiles. It then allows you to launch a campaign, and finally, generate and view reports on email opens, link clicks, submitted credentials and more.
This tool is very easy to use, which allows for quick execution; the idea behind Gophish is to be accessible to everyone. It’s free and offers Gophish releases as compiled binaries with no dependencies.
Main features include:
- Quick installation
- REST API
- Easy-to-use interface
- Binaries provided for Windows, Mac OSX and Linux
- Real-time reports
evilginx2
With conventional phishing techniques, having 2FA enabled on user accounts can mitigate most attacker tactics. This is where Evilginx2 can be quite useful. A successor to Evilginx, Evilginx2 is a bit different from other tools and simulators on this phishing tool list, in the sense that it acts as a man-in-the-middle proxy.
And how can this help with phishing campaigns? Well, in common phishing scenarios, you would serve templates of sign-in page lookalikes, but Evilginx2 works differently. It connects to websites that are protected with 2FA, becoming a web proxy between the phished website and the browser, and intercepting every packet, modifying it, then sending to the real website.
Additionally, it captures session token cookies that, if exported to a different browser, can give full authorization to access the user account.
Modlishka
Modlishka created quite a buzz when it was first released, as it demonstrated the ease of using phishing kits and the scope of their capabilities. It’s another tool that evades 2FA and doesn’t use any templates; to use Modlishka you only need a phishing domain and a valid TLS certificate, so there’s no time wasted by having to create phishing websites.
Modlishka is a reverse proxy that stands between the user and their target website. The user connects to the “attacker’s” server, and the server makes requests to the real website, serving the user legitimate content—but with all traffic and passwords entered being recorded by the tool. With it, you’ll automate the phishing campaign and make it more time-efficient.
From there, you can collect 2FA tokens and use them to access the user’s accounts and even establish new sessions. Some of Modlishka’s main features are:
- Pattern-based JavaScript payload injection
- Wraps websites with TLS wrapping, authentication, relevant security headers, etc.
- Stripping websites from all encryption and security headers
- Support for 2FA
- Credential harvesting
- Written in Go
Phishing Frenzy
Phishing Frenzy is an open source Ruby on Rails phishing framework designed to aid penetration testers and security professionals in creating and managing email phishing campaigns. By aiding in campaign management, generating detailed campaign statistics, and credential harvesting (among many other features), Phishing Frenzy makes the phishing process run more smoothly and efficiently.
Social Engineering Toolkit - SET
The Social Engineering Toolkit (SET) is a tool we’ve written a lot about, and we’re visiting it again here, this time as a phishing tool. SET is an open source Python security tool that features different attack techniques focused on penetration testing and using humans as its targets. Types of attacks addressed are, phishing (of course), spear phishing, web attack, infectious media generator, creating a payload, mass mailer attack and others.
As we’ve already featured a fully dedicated post on SET, we’ll only highlight its main features here, with details on installation and use cases, and a more in-depth review of the features we shared about in our earlier post. Main features (and some fun ones) of this phishing tool include:
- Multi-platform
- Supports integration with third party modules
- Fast-Track penetration testing platform
- Powershell attack vectors
- Website cloning
- Faking phone numbers
WifiPhisher
A really popular phishing tool, Wifiphisher has the ability to associate with a nearby WiFi network and obtain a man-in-the-middle position. It can do this in different ways: by using the Evil Twin attack that considers creating a fake wireless network to mimic a legitimate one; by using KARMA, where the tool acts as a public network; or with Known Beacons, where Wifiphisher broadcasts ESSIDs that seem familiar to the users.
For example, if Wifiphisher uses the Evil Twin attack to obtain the MiTM position, from there it will deauthenticate users from their access point, clone the access point and trick the user into joining the fake one which conveniently doesn’t have a password. It will then serve the user with a customized phishing page.
dnstwist
Dnstwist is a Python command-line tool that can help you detect phishing, URL hijacking, copyright infringements, domain squatting, fraud and more. It’s an easy-to-use tool for domain management as well as tracking if anyone is faking your brand and damaging your reputation.
It does this by generating permutations based on the target domain name using different techniques, and then checking to see if any of the variation is in use. It even checks to see if any web pages are used for phishing campaigns or brand impersonation.
Main dnstwist features include:
- A number of different domain fuzzing algorithms
- Unicode domain names
- Domain permutations using dictionary files
- Multithreaded task distribution
- Rogue MX host detection
- GeoIP location
SocialPhish
Authentic-looking websites are the key to a successful phishing campaign, and to effectively test awareness of and resilience to phishing, you’ll need good tools. That’s where SocialPhish can help.
Putting aside the need to create templates, it can clone a social media website that prompts users to reveal their credentials quickly, and then saves those credentials in a log that can be easily analyzed. This allows for the easy management of phishing campaigns and helps to streamline the phishing process.
It lacks proper documentation so you might find using some of its features a little tricky, but all in all it’s a solid social media phishing tool.
pythem
Pythem is a multipurpose penetration testing platform written in, you guessed it, Python. This framework can be used to perform different security tests and assessments that include simulating ARP spoofing, DNS spoofing, DHCP spoofing and SSH brute force attack, but can also perform exploit development and reverse engineering. Additionally, it can perform web application tasks such as web crawling, post scanning, redirecting to a fake page for credential harvesting, network sniffing and more.
EAPHammer
EAPHammer is a toolkit designed to perform evil twin attacks against WPA2-Enterprise networks. It’s an easier-to-use and more specific alternative to Wifiphisher that allows for easy execution of wireless attacks without the need for a lot of manual configuration. Types of attacks addressed by EAPHammer are KARMA, SSID cloaking, stealing RADIUS credentials, hostile portal attacks, and password spraying across multiple usernames against a single ESSID. Other features include:
- Support for WPA-EAP/WPA2-EAP
- No manual configuration necessary
- Support for evil twin and karma attacks
- Generates timed Powershell payloads for indirect wireless pivot
- PMKID attacks against PSK networks using hcxtools
SecurityTrails API
Having access to more than 400 million domains, and over a billion of tracked subdomains, along with DNS records and IP addresses, open ports, software versions, SSL certificates, domain DNS records and IP blocks can really help you enhance your attack simulation. With SecurityTrails API you will be able to integrate our data security into your application and query our intelligent database to boost your domain investigation tasks and track phishing domains. Main API features include:
- Current and historical WHOIS data
- Passive DNS
- Hostname data
SurfaceBrowser™
Once you’ve discovered suspicious and possible phishing domains, it’s time to take your investigation one step further and get the needed intel. SurfaceBrowser™ can provide you with data on the owner of the domain as well as other WHOIS data, all current and historical DNS records, nearby IP address ranges, certificate transparency logs and more. And what would you think if we told you that you can get all of this data in a single unified interface? You’ll also gain access to accurate IP geolocation, ASN information, IP type, and other IP tools. The main SurfaceBrowser™ features include:
- IP blocks
- SSL certificates
- Associated domains
- Open ports
- Reverse DNS
- Forward DNS
Phishing Catcher
Certificate Transparency logs offer domain security by monitoring for fraudulent certificates. Phishing Catcher is an open source tool that works by using the CertStream API to find suspicious certificates and possible phishing domains. To measure suspicion, they consider domain name scores that exceed a certain threshold based on a configuration file.
BlackEye
Blackeye, or as they themselves claim, “The most complete Phishing Tool”, is a bash script that offers 32 templates to choose from, and allows you to select which social media website to emulate. Five nights in anime for android.
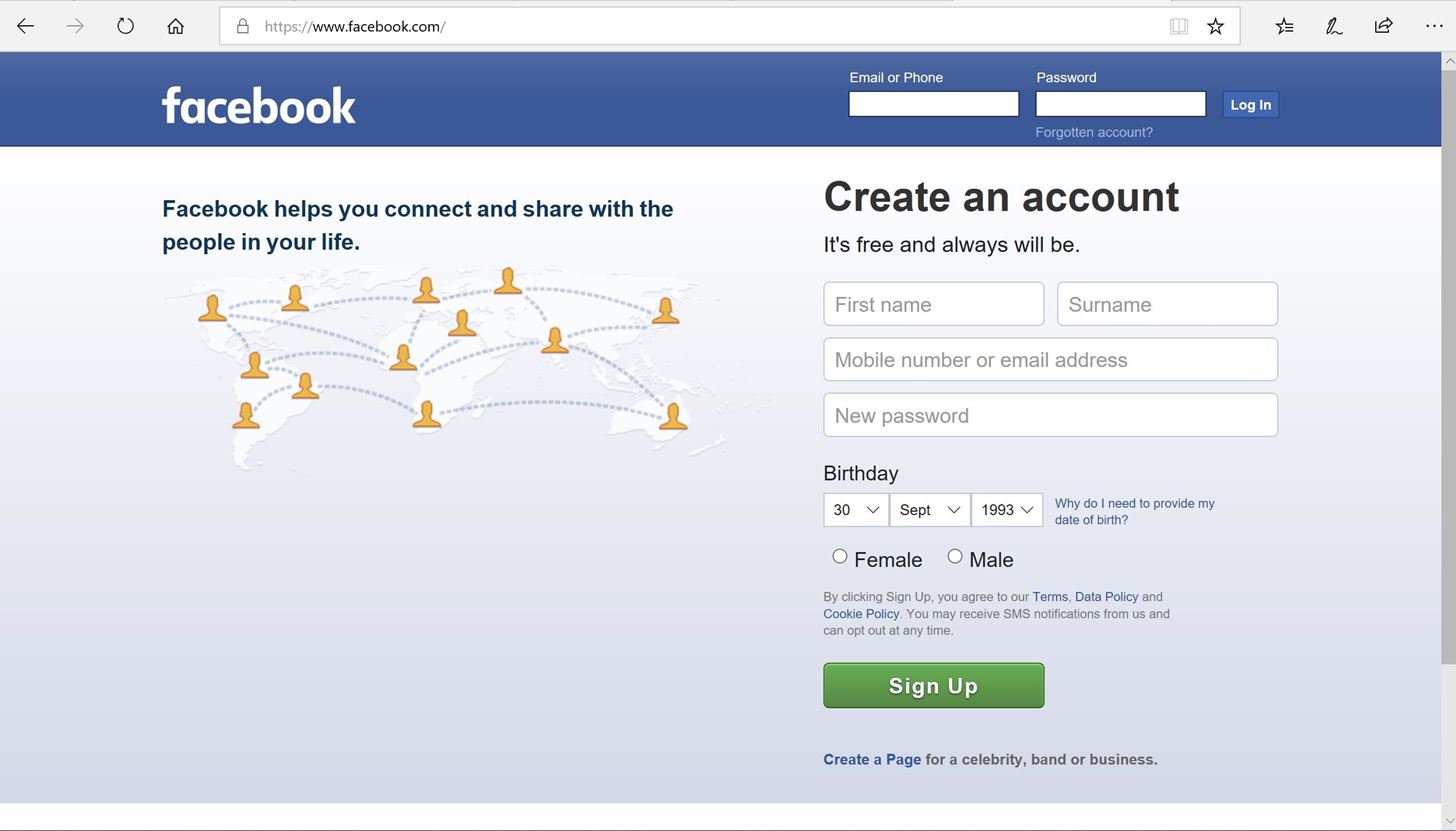
Websites included in the templates are Facebook, Twitter, Google, PayPal, Github, Gitlab and Adobe, among others. Once you choose a template, BlackEye will create a phishing website that can be connected to the target’s device, to collect credentials and redirect them to the legitimate website. While it may not be the most complete or ultimate phishing tool around, BlackEye is a great addition to your phishing toolkit.
HiddenEye
“The modern phishing tool”, HiddenEye is an all-in-one tool that features interesting functionality like keylogger and location tracking. It also offers a number of different attacks such as phishing, information collecting, social engineering and others.
HiddenEye supports all major social media and commercial websites such as Google, Facebook, Twitter, Instagram and LinkedIn, and they can be used as attack vectors. There are also several tunneling choices available to launch phishing campaigns:
- localhost
- LocalXpose
- Serveo
- Ngrok
- Localtunnel
- Openport
- PageKite
Additionally, HiddenEye can perform live attacks and collect IP, geolocation, ISP and other data, use the keylogger function as mentioned, and it has Android support.
ZPhisher
Zphisher is an upgraded form of Shellphish, from where it gets its main source code. This phishing toolkit offers different phishing templates (37 to be exact) of major websites including Facebook, Instagram, Google, Adobe, Dropbox, Ebay, Github, LinkedIn, Microsoft, PayPal, Reddit and Stackoverflow. ZPhisher also offers 4 port forwarding tools:
Phishing Page Maker Tools
- localhost
- Ngrok
- Serveo
- Localhost.run
CredSniper
Here we are again at bypassing 2FA and collecting 2FA tokens, but this time with CredSniper. Written in Flask, CredSniper helps red teams launch phishing websites with SSL which can be used to obtain credentials and with templates using Jinja2, it supports the capture of 2FA tokens.
Using their API, you get access to captured credentials, which in turn can be integrated into your own app by using a randomly generated API token. Some of CredSniper’s features include:
How To Make Phishing Site
- Fully supported SSL via Let’s Encrypt
- Exact login form clones
- Easy integration
- Customizing the templates
Phishing Page Creator Tool
One really interesting feature of CredSniper is its Gmail Module. It can detect 2FA, supports SMS, Google Authentication, and even U2F bypassing.
Final words
As the human side of security remains one of the top cybersecurity risks for any organization, and malicious actors constantly use phishing attacks that leverage on unsuspecting victims to obtain credentials, gain access to networks and breach organizations’ defenses, the use of phishing tools in security assessment and testing is crucial.

While this is far from an extensive list as there are so many phishing tools out there, aiding in many different phishing-related tasks and techniques, we hope that we’ve introduced you to a few new phishing tools that will enrich your security toolkit significantly.
Both SecurityTrails API and SurfaceBrowser™ are great additions to your phishing toolkit, each tailored to different IT and security roles. To learn more about them or any of our other reconnaissance, threat intelligence and attack surface reduction tools that will take your infosec tasks to the next level, contact our sales team for easy assistance.
Sara believes the human element is often at the core of all cybersecurity issues. It’s this perspective that brings a refreshing voice to the SecurityTrails team. Her ability to bridge cognitive/social motivators and how they impact the cybersecurity industry is always enlightening. Arena hearthstone app.